Cybersecurity training organization SANS Institute suffered a data breach after one of its employees was the victim of a phishing attack.
SANS Institute, one of the largest organizations that trains information security specialists around the world, has itself suffered from a cyber attack. Attackers gained access to SANS data after one of her HR employees fell for a phishing attack.
On August 11, SANS reported that the attacker gained access to the email account of one of the employees and set up the redirection of all correspondence received on the attacked mailbox to some other address, and also installed a malicious add-on for Office 365.
As a result, the hackers received 513 letters, which contained a total of about 28,000 records of the personal information of SANS members. This information does not include passwords or financial information such as credit cards. The data includes email addresses, full names, phone numbers, job titles, company names, and physical addresses.
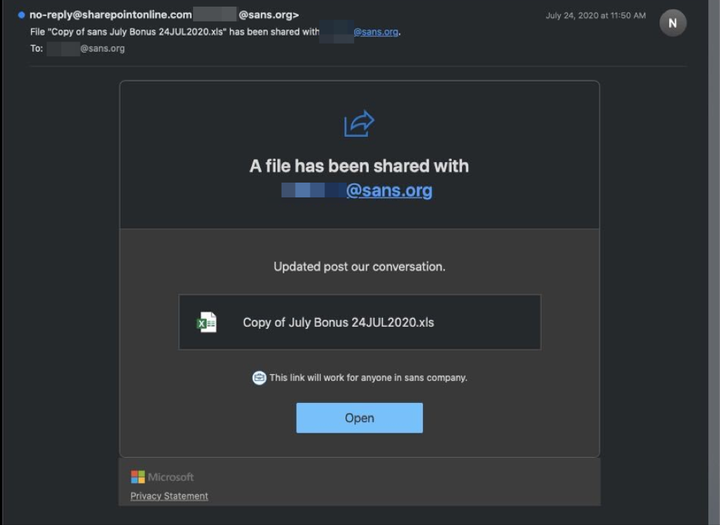
According to the SANS investigation, the attack began with a phishing email posing as a file allegedly sent by the SANS SharePoint service.
The file was called "July Bonus Copy 24JUL2020.xls" and the email prompted the user to click the "Open" button to access the file.
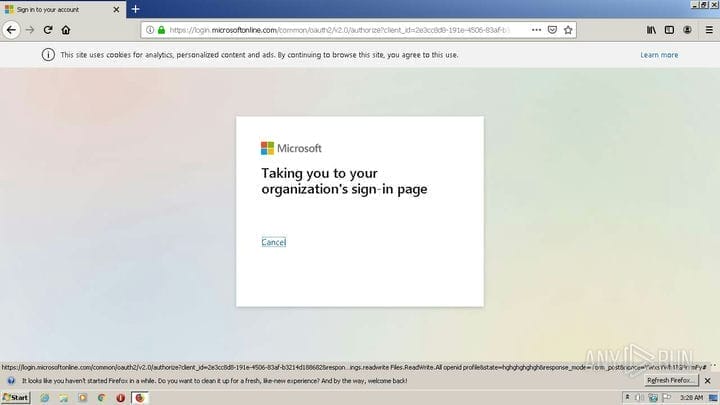
Clicking the button opens the default browser at "https://officei6zq49rv2p5a4xbq8ge41f1enjjczo.s3.us-east-2.amazonaws[.]com/index.html" which prompts the user to enter their Office 365 credentials.
In parallel, a malicious add-on for Microsoft Office OAuth was installed, called Enable4Excel.
Once installed, it adds a new forwarding rule named Anti-Spam Rule that monitors for specific keywords in emails. If a matching keyword was found in the email, it will be redirected to the external address daemon[@]daemongr5yenh53ci0w6cjbbh1gy1l61fxpd.com.
Here is a list of monitored keywords:
agreement
Bank
bic
capital call
cash
Contribution
dividend
fund
iban
Payment
purchase
shares
swift
transfer
Wire
wiring infoBased on information from VirusTotal, the phishing campaign was carried out on July 24, 2020. SANS wasn’t the only target, at least two other companies uploaded similar emails to VirusTotal.