In this article, we’ll show you how to check your phone, laptop, and online accounts to make sure no one is spying on you.
Whether it’s a nosy boss or a paranoid partner, no one should be spying on your phone or laptop. But this can still happen if stalker software is somehow installed on your devices. These programs are specially designed to be difficult to detect, but you can find them if you know how.
Working with programs installed on corporate devices by your employer is a little different from those installed by those you know personally who are trying to spy on you. The company you work for may have good reasons to monitor your performance, especially if it provides the hardware and software you use every day.
Whether or not such monitoring is warranted, at the very least your superiors should let you know what they are monitoring, not keep it a secret.
This guide focuses on the software, with a focus on stealth, but remember that there are plenty of legitimate parental control apps and built-in tracking tools (like Apple’s Find My) that your family members can use. The difference is that it’s very easy to understand if these types of applications are currently working, but you still need to know about them and how they can be used.
How to check your phone
The good news for iPhone users is that it is almost impossible to install stalker software on iPhone: Apple has set strict app access and app security restrictions, which are not always user-friendly, but very effective for security. iOS just doesn’t allow apps to get deep into the system to be able to secretly control what you do on your phone.
There is one exception, and that is if your iPhone is jailbroken (unlocked so you can install any apps). A person who wants to install surveillance on your smartphone in this way needs to be tech-savvy and have physical access to your phone for an extended period of time. The easiest way to check is to find the Cydia and SBSettings apps on the home screen .
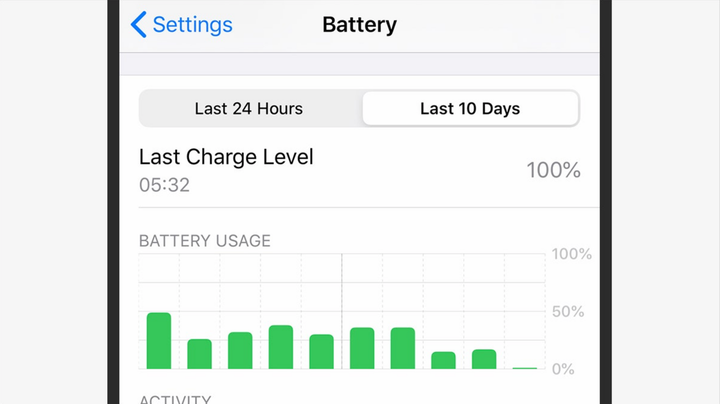
Decreased battery life is one of the signs that your phone has been compromised. Screenshot: David Nield | Wired
If you find your iPhone has been jailbroken, a hard reset should fix it (and wipe everything else, so make sure your important data is backed up).
Installing stealth surveillance apps on Android devices is somewhat easier, though it’s officially banned: Google will remove apps from the Play Store if it finds evidence of stalker -like behavior. However, applications still sometimes slip into the market.
An attacker will still need access to your phone in order to install tracking. This is actually one of the biggest warning signs to look out for: if you set up your Android smartphone yourself and no one else has used it for more than a few seconds, it should be free of stalker software.
If your phone has been jailbroken, you may notice that it heats up or the battery drains quickly when you are not using it. You may also see unusual notifications that you don’t expect, or the startup time is taking longer than it should. Stalking apps are designed to be difficult to detect, but if you notice any unusual phone behavior, it’s worth looking into.
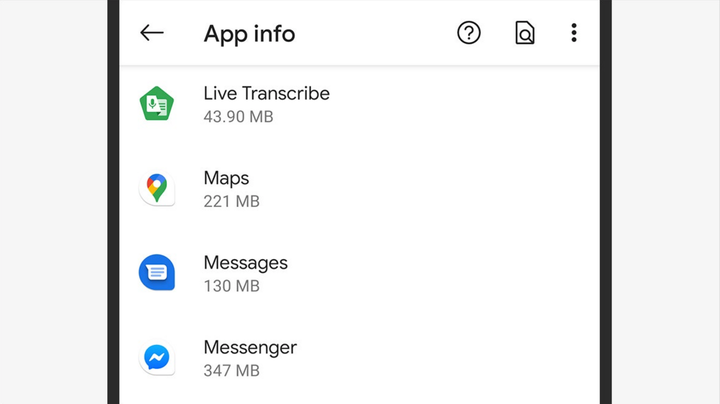
Check the list of applications to find anything suspicious. Screenshot: David Nield | Wired
Monitoring apps very often hide their presence, but they can show up in the app list under a harmless alternative name: in Android settings, tap Apps & notifications, then See all apps. Stalker software can also be hidden in the Android settings menu itself (often in security-related sections) – look for menu items that don’t look right, or that you didn’t notice before, or that don’t match the official documentation.
For added peace of mind, you can take the help of third-party tools: Incognito, Certo, and Kaspersky Antivirus are three phone scanning apps that should tell you if you have malware on your device.
It should be noted that the problem of stealth surveillance apps is more acute now than ever, and both Google and Apple are very negative about any application that tries to do something like this.
How to check your computer
Most of the same Android and iOS stalker detection principles apply to Windows with macOS. You still need access to your computer to install tracking, but attackers can also trick you into installing a virus under the guise of something ordinary.
Also, installing tracking software is easy for an IT manager who sets up a work laptop for you. As always, protect your laptop or desktop well with your own account and password, and pay attention to its physical security, such as who has access to it and when.
How to protect data on your laptop
Your laptop is a treasure trove of personal and confidential information – make sure it is as secure as possible.
Both Microsoft and Apple understand the problem of stalker software very well, and Windows and macOS will detect and block some hidden tools without any further help. Like any other type of malware, stalkerware can be detected by third party antivirus like Norton, Bitdefender or Malwarebytes, which have versions for both Windows and Mac.
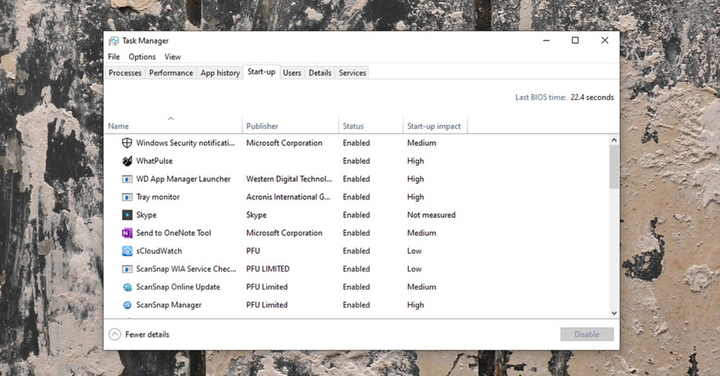
Task Manager shows what is running in Windows at the moment. Screenshot: David Nield | Wired
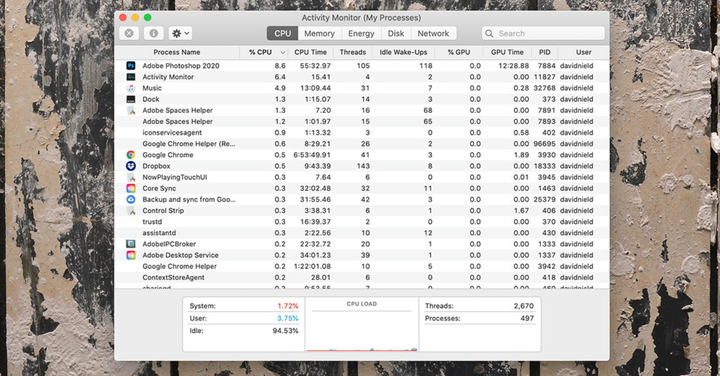
If you’d like to investigate on your own, open Task Manager in Windows (search for it in the taskbar search box) or Activity Monitor in macOS (search for it in Spotlight with Cmd + Space) to see everything running on your computer. Be aware that spyware does not usually list itself under its real name and may well try to impersonate a system application or use a short name that you probably won’t notice.
Review all the tabs that appear in the dialog box on the screen. If you see something you didn’t install, or something that seems suspicious in its behavior (probably excessive disk usage), then do a quick web search for the application or process name. Usually this is enough to understand what you are dealing with.
You should also check to see if applications and processes are running at the same time as your operating system, as most surveillance tools should. On Windows, you’ll find a list of startup software in the Startup tab of the Task Manager; on macOS, open System Preferences, then select Users & Groups and Login Items. Again, if you see an application that you are not sure about, look on the Internet.
The macOS Activity Monitor tells you what’s going on with your system. Screenshot: David Nield | Wired
On macOS, some additional permissions for stalker apps may be required: in System Preferences, go to the Security & Privacy section and then to the Privacy section. Check the entries for input monitoring and full disk access as spyware often requires these permissions. Windows doesn’t have such a setting, but you can see the permissions that apps have (including location, camera access, etc.) by selecting Privacy from the Settings menu and scrolling down to App Permissions.
As we said, if your employer is monitoring your work day, the tools must be visible and work with your consent. But if you’re really worried, a full system reset for Windows or macOS should clear most of the hidden monitoring tools if you suspect one of them has gained root access (make sure you back up your files first).
How to check your accounts
For those who want to invade your privacy, it is easier to simply access your online accounts than to try to install wiretapping on your devices.
In addition to checking for unauthorized access to your devices, you should also periodically check for unauthorized access to your accounts. Obviously, this starts with protecting your usernames and passwords: make sure they are known only to you, they are hard to guess, they are not used in multiple accounts, and they are not recorded anywhere.
Consider using a password manager to keep your passwords secure. For accounts where it’s available, turn on two-factor authentication.
Facebook will show a list of all the devices you are signed in on. Screenshot: David Nield | Wired
If there is an unwanted guest in your account, you can find confirmation of this in these settings. For Facebook, for example, open the settings page in your browser and click on Security and Log in to see all the devices your account is active on (and log out on which you are not logged in). If you’re using Gmail on the web, click the Details button in the lower right corner to view other active sessions.
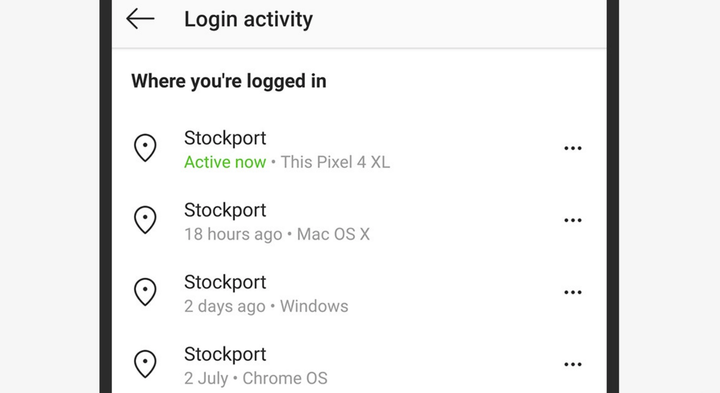
Some mobile apps, like WhatsApp and Snapchat, can only be used on one device, so you know the login you’re using is the only active one. However, this doesn’t apply to all apps – on Instagram, for example, if you open the app’s settings and then tap Security and Login Activity, you’ll see a list of all the devices associated with your account. To remove a device, tap the three dots on the side of any of the entries and tap Log out .
We also recommend that you view activities in your accounts, such as activities such as the sent emails folder in your email account, or messages received and sent on Twitter or Facebook Messenger. It’s also worth checking the drafts and trash folders in your accounts for signs of suspicious activity.
Check Instagram to see recent login activity. Screenshot: David Nield | Wired
If someone did gain access to your email account, they most likely set up the automatic forwarding to other mail feature, and this should definitely be checked. For example, on the web version of Gmail, click the gear icon (top right), then View all settings and then Forwarding and POP/IMAP: look at the entries under the Forwarding heading to see if your emails are being sent where something else. Also check the Filters and Blocked Addresses tab for anything you haven’t configured.
The approach may vary slightly depending on the apps you use and the accounts you have, but staying on top of your active logins and monitoring app activity is the best way to spot unwanted visitors. Changing your password regularly is the most effective way to block unwanted access to your accounts.
This article is a manual translation of material from Wired magazine.