Link previews are an undeniably handy feature. However, it can also compromise privacy and security.
Link preview (or preview) is a feature found in just about every modern messaging app, and it’s not just there. It simplifies online conversations by showing a brief description of the site, a thumbnail image, or both images and text associated with the linked file.
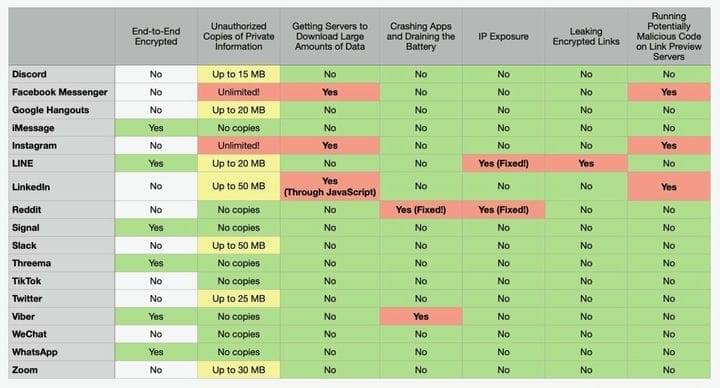
Unfortunately, they can also give away our sensitive data, consume internet, drain smartphone batteries, and even open links in end-to -end encrypted chats. According to a study published on Monday, the most serious violations were found in messengers Facebook (no doubt), Instagram, LinkedIn and Line.
How does preview work?
When the sender includes a link in a message, the app accompanies it with a title, short text, and an image. It usually looks something like this:
For this to happen, the application itself, or a proxy server assigned to it, must follow the link, open the file or website there, and see what it contains. And this is precisely what makes users vulnerable to attacks. The most dangerous apps are those that allow you to download malware, while others can be forced to download files so large that they cause the application to crash, drain your battery, or consume limited Internet traffic.
And if the link leads to private content, such as a tax return posted to a private OneDrive or DropBox account, the app server can view and store it indefinitely.
Researchers Talal Haj Bakri and Tommy Mysk, who produced the report, found that Facebook Messenger and Instagram had the most abuse. As shown in the video below, both applications download and copy the entire linked file, even if it is measured in gigabytes. And that can be a problem if users want to keep the file they send private.
Instagram servers will download any link sent in private messages, even if it’s 2.6 GB.
By downloading these attachments, applications can consume a huge amount of Internet traffic and battery power. Both applications also run any JavaScript contained in the link. The problem is that users do not have the ability to check the safety of the JavaScript code on the site, and cannot expect instant messengers to have the same exploit protection on board as modern browsers.
Hackers can run any JavaScript code on Instagram’s servers.
Haj Bakri and Mysk reported their findings to Facebook itself, but the company said both apps were working as expected. LinkedIn fared a little better. The only difference was that instead of copying files of any size, it only copied the first 50 megabytes.
Meanwhile, when the Line app opens the encrypted message and finds the link, it sends it to the company’s server to generate a preview.
“We believe this defeats the purpose of end-to-end encryption, as LINE servers know all about the links that are sent through the app and who is passing which links to whom," the researchers wrote.
Discord, Google Hangouts, Slack, Twitter, and Zoom also copy files, but they limit the amount of data to between 15MB and 50MB. The table below provides a comparison of each application included in the study.
Overall, the study is good news, as it shows that most messaging apps work correctly. For example, Signal, Threema, TikTok, and WeChat give users the option not to get link previews. For truly sensitive messages and users who want maximum privacy, these are the best options. After all, even if there is a preview in it, these applications use relatively safe means to render them. Unfortunately, Tommy and Hajj did not include Telegram in their study.