Lightshot generates public URLs that are easy prey for scammers.
People, in the dark, themselves share their sensitive information online when they use the popular Lightshot screenshot app. The URLs of dozens of screenshots taken with the app can easily be found online, making them easy prey for cybercriminals.
The Lightshot app, owned by software development firm Skillbrains, is popular with millions of people who receive and send dozens of screenshots every day. By taking a screenshot, a person can upload their image to the company’s server with a public URL. It is possible to save a screenshot to your phone or share it on a social network.
The URL is also needed so that users can send their screenshots to friends, family or colleagues. Lightshot has already uploaded over two billion screenshots to the web. However, the process of how the URLs themselves are generated leaves much to be desired.
All screenshot links have a simple format: " prnt.sc/" (Lightshot server) + a six-character alphanumeric code. This means that anyone can enter "prnt.sc/" and a random combination of six numbers and letters and stumble upon another user’s uploaded screenshot. Such situations have repeatedly happened during the entire existence of the program on the market.
The first release of Lightshot took place in 2014. Since then, the application has been actively developed and became available as extensions for browsers and a desktop version for the OS. The program is compatible with Mac and Windows, and also has plugins for Chrome and Firefox. Over a million people use this add-on on Google Chrome and about 40,000 on Firefox. On Android phones, the app has been installed from Google Play over 500,000 times.
If you look at the results of 11,000 randomly generated URLs created by the system that Lightshot uses, you can easily find private photos of its users. Most of the links don’t work, of course, because the screenshots have already been removed or can no longer be found. However, many URLs belong to screenshots that include names, addresses, contact numbers, bank details, and even intimate parts of the body of app users.
The automated script found 529 showable images out of 11,000 generated URLs. About 63% of those screenshots contained absolutely useless information: clips from video games, wish lists, coding instructions.
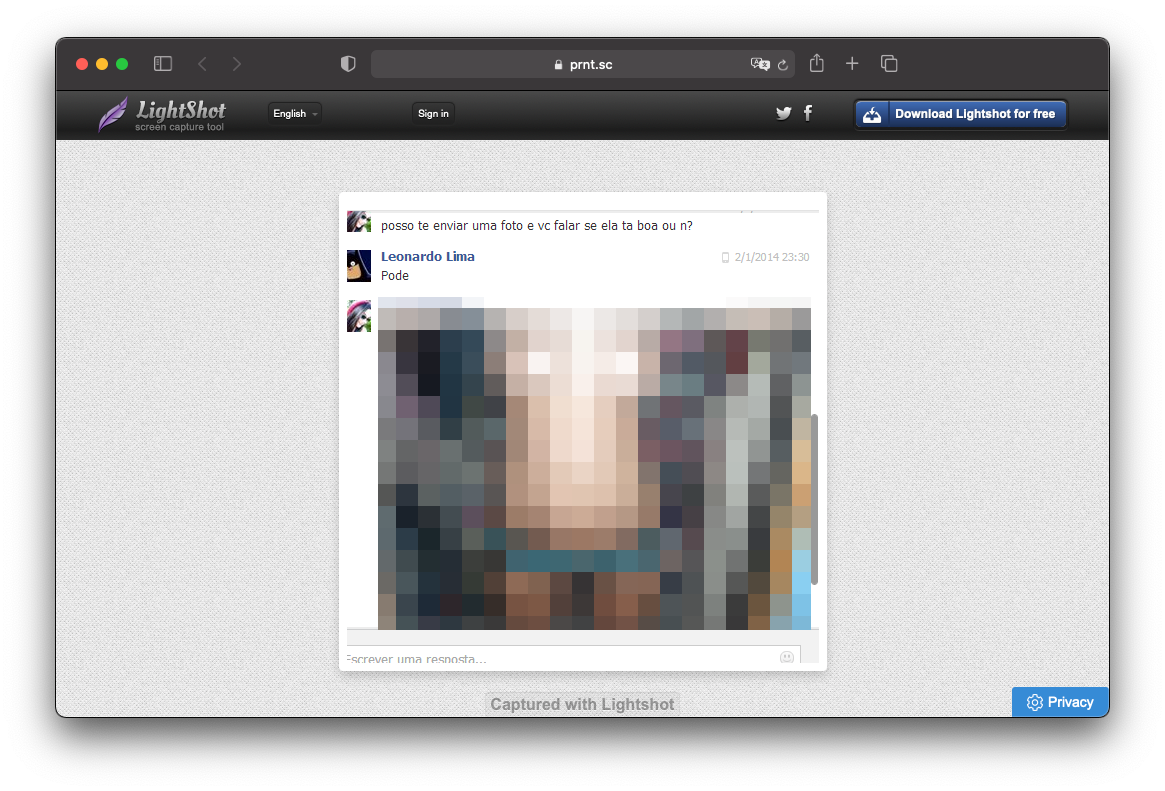
About 20% of the analyzed images included data that could be used to steal personal information or hack into other accounts. People shared snapshots of conversations, emails, and social media posts with friends using identifiable usernames.
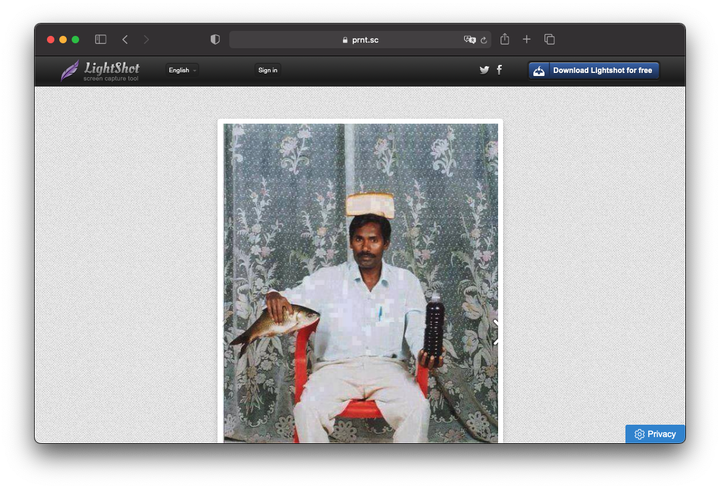
The analysis showed that 8% of the screenshots contained more personal, private information. Among them are intimate photos that were taken during video calls; 6 screenshots of users as children and 30 images clearly showing the names, registration and bank details, phone numbers, IP addresses and delivery addresses of people.
“Giving public access to sensitive user data is unacceptable. This happens because digital platforms save money on protecting the personal information of their customers."
According to Bhagya Wimalasiri, an advanced systems security researcher at the University of Sheffield, such platforms are built on models that monetize the ” idea of insecurity ” itself. Without thinking about the safety of the user, such applications expand their functionality in order to attract more customers. One of these "chips" are screenshots with public access.
Skillbrains, which owns Lightshot, has yet to comment. However, the app’s terms of use notes that all uploaded images are not private. “The screenshot will be available to anyone who enters its exact URL. No image uploaded to our site can be private," the program’s security policy says. "Our site is designed to share photos, not protect them from external threats."
The fact that anyone can find sensitive photos on the Lightshot website is no big secret. Through a practice such as web scraping, a person can get around 13,000 links to publicly available screenshots. Moreover, there are special programs that will help analyze the received images for personal data and intimate photos.
Lightshot’s terms of use also state that users are prohibited from uploading photos that contain adult content or depict a violation of the law. However, not everyone follows these rules. It’s also worth noting that neither the Lightshot app itself nor its website homepage clearly states that all screenshot URLs are public.
Such carelessness allows criminals to carry out many different attacks. With the right information, they can steal your credentials, withdraw money from your card, or carry out banal phishing.
Customers and the company itself are jointly responsible for preventing the disclosure of personal information. People should be aware that their photos become public immediately after uploading. They should also be a little more careful about the screenshots they upload to the site.
Based on Wired UK.