Since ancient times, people have learned to protect information by converting it so that unauthorized persons do not have the opportunity to read it. Cryptography arose approximately when people only learned to speak. Moreover, at first, writing itself was a cryptographic system, since it could only be owned by selected people who had access to the study of cryptography.
Cryptography methods
A cryptographic method of information protection is a number of special methods of encoding, encryption or other transformations of information that make its content inaccessible to persons who do not have a cryptogram key. Cryptography and encryption are the most reliable methods of protection, since the encryptor protects the information itself, and not access to it. For example, reading an encrypted file will be impossible even if an attacker manages to steal the media. The implementation of this protection method is carried out using programs or software packages.
But, despite all the variety of applications, there are currently only a few encryption methods. All these cryptography methods belong to two types of cryptographic systems: symmetric (with a secret key) and asymmetric (with a public key).
- Symmetric systems allow you to encrypt and decrypt information using the same key. It is impossible to decrypt the secret key cryptographic system if the decryptor does not have the secret key.
- In public-key cryptographic systems, users have their own public and private keys. All users have access to the public key, and information is encrypted using it. But for decryption, a private key is required, which is held by the end user. Unlike cryptograms with a secret key, in such a system, the participants are not two, but three parties. The third one could be a cellular provider or, for example, a bank. However, this party is not interested in stealing information, as it is interested in the correct functioning of the system and obtaining positive results.
Types of cryptography
The advantage of any modern cryptographic method is the possibility of providing a high guaranteed strength of protection, calculated and expressed in numerical form (the average number of operations or the time required to decrypt secret information or select keys). Currently, there are the following types of cryptography:
- Information encryption.
- Information encoding.
- Dissection of information.
- Data compression.
Video about cryptography and encryption
Encryption
During the encryption process, a cryptographic transformation of each character is performed in the encrypted message. Among all known encryption methods, the following five main groups can be distinguished:
- Replacement (substitution). In turn, there are simple (single-alphabetic), multi-alphabetic single-loop ordinary, multi-alphabetic multi-loop and multi-alphabetic single-loop monophonic substitutions.
- Permutation. Distinguish between simple, complicated according to the table and complicated according to the routes of the permutation.
- Analytical transformations are carried out according to special dependencies or using the rules of matrix algebra.
- Gambling – Encryption is done with short or long finite gamma or with infinite gamma.
- Combined—messages are encrypted using substitution and permutation, substitution and gamma, permutation and gamma, or double gamma.
Message Encoding
This type of crypto transformation uses the replacement of some data elements with certain codes (for example, it can be combinations of numbers and / or letters).
Information dissection
In this method, the protected information is divided into separate data arrays, decrypting only one of which will make it impossible to disclose classified information.
Message compression
The compression method provides for the replacement of repeated sequences of characters in the protected data with smaller sequences. The efficiency of such compression depends on the number of identical sequences in the protected text.
Cryptography for beginners
Throughout the centuries-old history of cryptography and until now, this art has not been accessible to everyone. As a rule, these methods were used by people who did not go beyond the boundaries of the residences of the heads of powers, embassies, and intelligence agencies. And only a few decades ago, cardinal changes began to occur in this area – information became an independent commercial value and turned into a widespread, almost ordinary commodity. It is produced, stored, transferred, sold, bought, and, accordingly, stolen and forged. That is why today there are a large number of tutorials and computer programs designed for ordinary users who are interested in cryptography. Learning some simple types of encryption can be mastered even by a schoolboy.
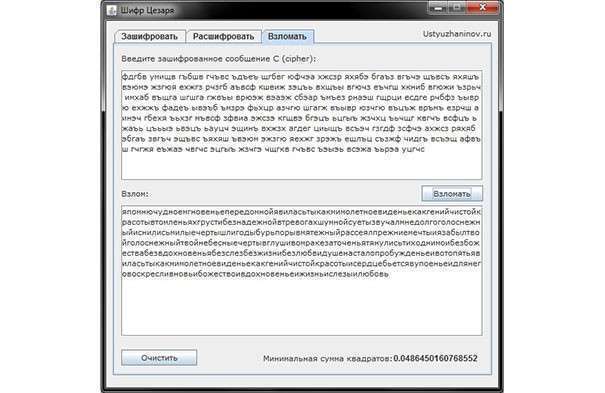
Caesar Cipher Program
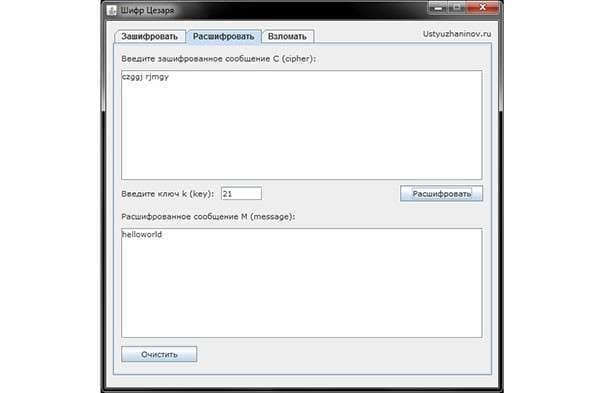
This encryption method is also called a shift cipher. In the software version, the Caesar cipher is a substitution cipher with a key, the characters of which are replaced in the text by characters located at some constant number of positions to the left or right of it in the alphabet. For example, a cipher with a shift to the right by three positions: the letter A is replaced by the letter G, B – by D, etc. It should be noted that the letter Y is not used in encryption and is replaced by the letter E.
Program:
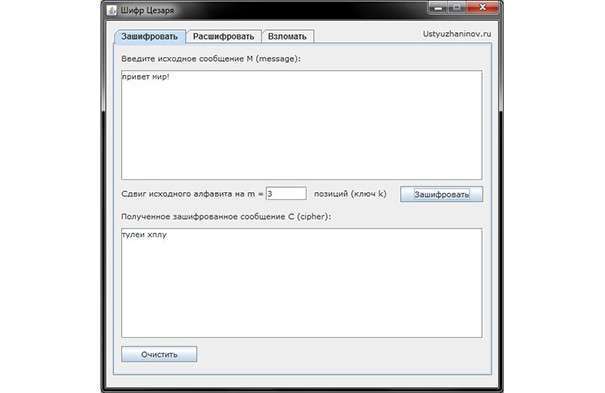 Encryption:
Encryption:
Decryption: