How technology has evolved to allow people to remotely access the desktop of other users, and why it is important to take care of proper security measures during this process – we will talk in this article.
“One of the conclusions that we all may have to come to in the future is that it is worth returning to the standard way of processing data and information flows from terminals and computers connected to the global network"
This is an excerpt from a document called " Request for Comments " dated 1971. It published a proposal to create an official communication protocol for the Telnet network, a key technology for gaining access to someone else’s computer through a command line interface remotely. It should be noted that the strategy proposed at that time differs from the concept that is used when creating modern tools for accessing a graphical interface remotely. However, many of the methods presented in this document are still in use today. Their main difference is that modern tools are compatible with several platforms at once.. This gives the user the ability to instantly switch between different operating systems.
“After I establish a connection and connect to your computer, I can do whatever I want! I wonder if I should enter the command " format c: " ("format drive C")? I’m still that crazy!"
No Windows, No Problem: The advent of remote access software dates back to the days of DOS
Remote access has been the focus of the programmer and developer community for many decades. This topic has been of interest since the days when people were first able to access mainframe networks using primitive terminals. The very idea of connecting to a computer remotely, as if a person is physically in the room and has full access to it, still seems a little magical to some users. However, this became possible already several decades ago.
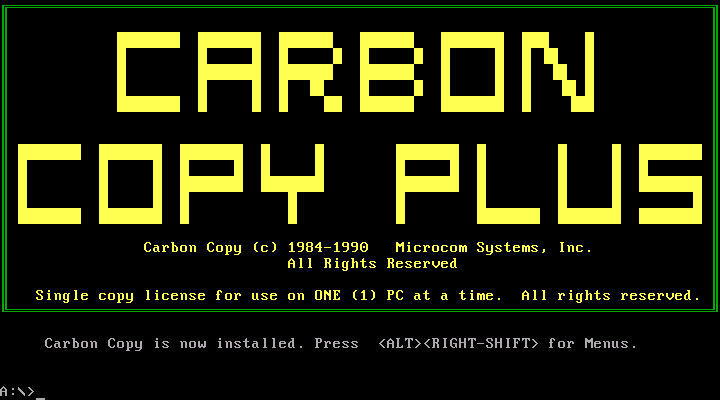
A key tool in the history of remote access software is Carbon Copy. This is the first program that allowed users to access their computers from a distance and control them in exactly the same way if they were in the room next to their PCs. This software was talked about back in the mid-80s – it was developed by Meridian Technologies and used a special technology: remaining resident in DOS memory, the program allowed users to call a PC over a telephone line and control the machine remotely.
It was an impressive stunt for its time. Many experts did not understand how this was possible in principle. For example, a spread in PC Mag magazine, published in March 1986, was devoted to a shocking program. It has been described by the author as " a new technology that is still secret to most users ".
And this is an advertisement for a new version of the program called Carbon Copy Plus. It publicizes the fact that a person can control two computers at the same time using only one copy of the software.
Carbon Copy, whose importance was recognized by media giants such as InfoWorld, became the market leader the following year (1987). Moreover, other similar tools began to appear, such as Norton ‘s pcANYWHERE. The Internet was then a new phenomenon, so these programs worked using standard modems. Users needed to directly call the computer using a telephone connection.
Unfortunately, a product called Carbon Copy fell victim to piracy. It is worth noting that in the history of Meridian Technologies there was even such a moment when it called on users of their software to turn in their colleagues. For information about illegal actions, you could get a rather big reward.
“We really do our best to create a good product, and all we ask in return is that people act honestly and do not use pirated versions of the program,” Charles Jones said in an interview with PC Mag. “Unfortunately, the world is the way it is and it is quite expected that we will have to pay some people $2,500 for information about violators”
Timbuktu Pro
Being able to access more powerful computers remotely was extremely tempting, especially with a graphical interface. A 1988 article in InfoWorld magazine featured a new Mac-based remote access tool called Timbuktu. It worked both over a local network and using modems, and was advertised to users as a program for remote access to more powerful and newer computers in the presence of a weak PC.
“For about the price of an SE, you can get Mac II hardware,” said Reese Jones of Farallon, which at the time had poached Timbuktu from Timbuktu, the creator of WOS data systems.
An example using the DOS version of pcAnywhere
Of course, the technology itself did not stand still and evolved over time: tools such as pcAnywhere soon appeared ; they made a huge leap from DOS to Windows. In general, remote access tools have been gradually getting rid of the dependence on a specific platform, which made it easier to manage computers outside the office.
As a result, remote access tools have become a key toolkit for IT teams around the world.
Five Popular Remote Access Software You Should Know About
- Chrome Remote Desktop. Most of Google’s advertising campaigns these days boil down to, "If you have our web browser, you can use this feature." This also applies to Chrome Remote Desktop, which has been around for over a decade and is arguably the easiest way to remotely access a computer in the world.
- GoToMyPC. This tool became popular at the end of the 20th century because it was easy to use and was used by millions of office workers around the world. Now the program has been greatly “pumped” and has many additional functions.
- Apple Screen Sharing. Apple has had a solid remote desktop app for a long time. However, it tends to go unnoticed by regular users because it has too many unnecessary features. A simpler and more efficient version can be called the Screens program, available in the Apple store.
- Remote Desktop Services. Microsoft also has its own computer screen sharing tool. Its history dates back to the days of Windows NT Server 4.0, which was released a quarter of a century ago.
- teamviewer. A tool for sharing your computer screen. It is commonly used by IT teams for technical support and remote desktop management. The program has gained its popularity in recent years due to its flexibility and ease of use.
1998
This is the year that the RFB (” remote framebuffer “) protocol first became available worldwide. The technology, developed in the English research laboratory Olivetti in the 90s, had deep roots. It was first used to create an interface that allowed a peripheral device to connect to the ATM operating system. This particular use case for this technology eventually led to the emergence of VNC (Virtual Network Computing), perhaps the most widely used public standard for remote access today. The research laboratory, which was later bought by AT&T, became the starting point for the creation of RealVNCin 2002.
The infamous Back Orifice hacking tool has common roots with modern remote desktop management software (according to this source ).
The problem with remote access is that it’s too easy to use for fraudulent purposes.
You probably don’t expect this article on the history of remote access tools to be about politics. However, a couple of years ago, former presidential candidate Beto O’Rourke made a claim that he was once a hacker.
O’Rourke was a member of the Cult of the Dead Cow (cDc), a hacker group known for their work in the information security field. It is worth noting that Beto himself talked about this more than actually engaged in hacker practice.
Many cDc members not named Beto O’Rourke also have successful careers. For example, a leading member of Mudge (birth name Pater Zatko) once worked for DARPA and now heads security for the social network Twitter.
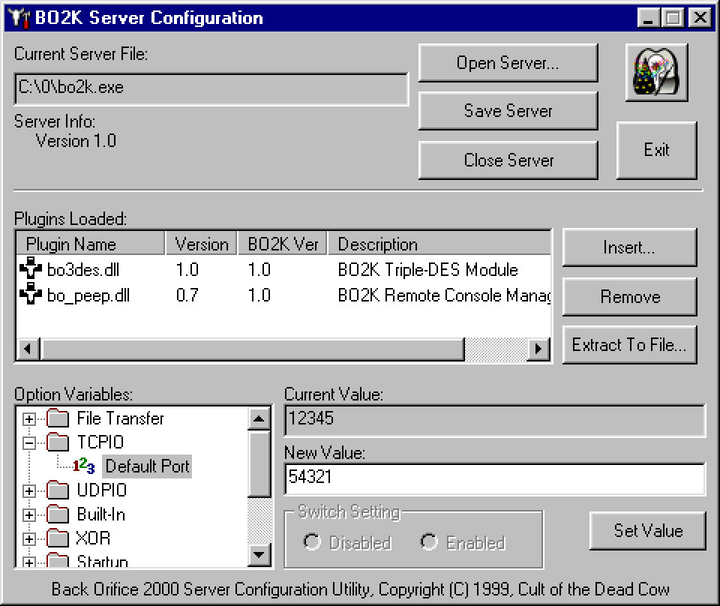
Before Beto drew attention to this hacker group, she was best known for creating one of the most memorable tools of the last 30 years, Back Orifice. This is a program for obtaining remote access to a computer. It opened a ” backdoor ” for hackers and made it possible to have full access to a PC running on Windows. This tool, which was first announced at the DEFCON event in 1998, was created to get Microsoft to think about stronger security measures for their operating system.
However, the company did not take the emergence of a new tool seriously, and then the hackers released an updated version of the program, which was even more dangerous for Windows. The threat was that with the help of Back Orifice it was possible to "weaken" the user’s system and easily manage it the way the hacker needed (invisibly to the owner ).
The strange thing is that, being a hacking tool, Back Orifice is not so different from modern remote system administration programs. It also provides the user with in-depth access to the OS of a remote machine.
The difference lies in the context in which the tools are used, as well as in the approach to the security principles themselves. At this point, remote access is (generally) very secure for the user. With it, the administrator can make important changes to the system. It is worth noting that, unlike the tools of the past, now all this happens with the help of secure tools that are protected from hacking.
TeamViewer
As a result, tools like TeamViewer have become incredibly common in the information technology industry. However, there are nuances in their work that relate to just an insufficient level of security when establishing a connection with a PC remotely.
For example, Symantec, the developer of pcAnywhere, discovered about nine years ago that its source code had been stolen and published in The Pirate Bay. This happened after the hacker failed to get money from the company during another extortion. After this embarrassment, pcAnywhere software, which appeared on the market back in the late 80s, was completely withdrawn from sale.
“Many companies are using remote access to make life easier for their employees working from home. However, by using such practices, they are more likely to become victims of hackers in the future,” Matt Ahrens, head of the information security group at the Cyber Insurance Coalition, wrote in a 2018 article for DarkReading.
Of course, given this risk, companies should choose software that is constantly evolving in terms of security and connection protection. That’s why the Florida water treatment plant incident is a perfect example of how not to control access to a remote computer.
TeamViewer with a default password – you probably don’t want to see the management of software that ensures the operation of critical infrastructure, such as water supply in the city. But unfortunately, that’s the way it was.
768%
Made up the growth in the number of attacks on RDP-based clients in 2020 (according to ESET ). The problem is that many people are at a distance from each other all the time. Hackers use this situation to sow chaos and panic. Therefore, if you do not need remote access, then it is better to disable VNC.
Conclusion
Remote access software is incredibly useful if it falls into the right hands. For example, you can use it to control access to your server as needed. At the same time, if such tools become a godsend for hackers, then this can lead to unpleasant consequences.
You need to understand that such programs allow people to manage the critical security systems of their OS remotely. It is important that unique logins and passwords are used and that all security measures are taken when connecting to a PC located in another location.
Based on materials from Tedium.