Only one image file was needed to implement the now fixed RCE vulnerability.
Facebook has fixed a critical vulnerability in Instagram that could lead to remote code execution and capture of cameras, microphones, and even the entire smartphone, according to ZDNet
The security vulnerability was reported by Check Point. The vulnerability is described as a "critical vulnerability in Instagram’s image processing".
The vulnerability has received the identifier CVE-2020-1895 and a CVSS score of 7.8. Facebook’s security advisory states that this vulnerability is related to a stack overflow.
“A large stack overflow could occur on Instagram for Android when attempting to upload an image with custom dimensions. This works on versions prior to 128.0.0.26.128," the post reads .
In a blog post Thursday, Check Point cybersecurity researchers said sending a single malicious image was enough to take over Instagram. The attack can be triggered by sending the created image – by email, WhatsApp, SMS or any other communication platform – and then stored on the victim’s device.
See also: How much do top hackers earn from rewards for found vulnerabilities.
Whether the image is saved locally or manually, simply opening Instagram after that is enough to execute malicious code.
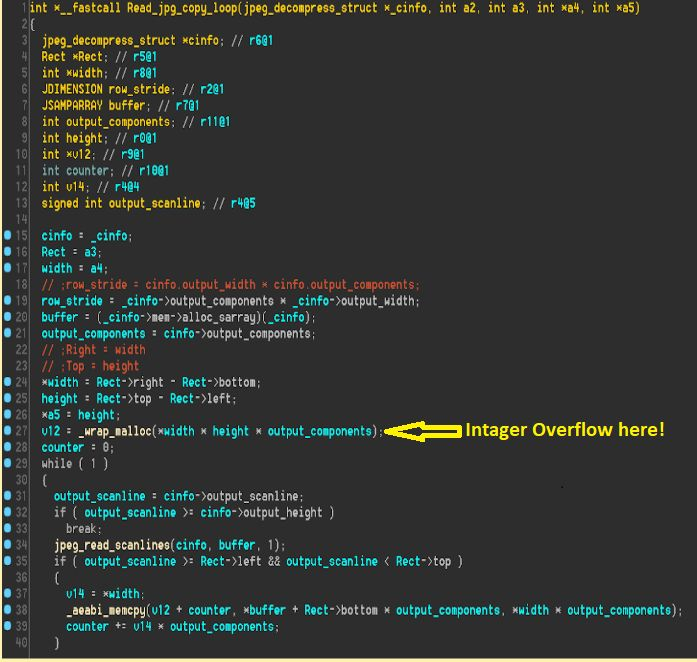
The problem is how Instagram handles third party libraries used for image processing. In particular, Check Point focused on Mozjpeg, an open source JPEG decoder developed by Mozilla that was being misused by Instagram to handle image uploads.
They found that the image sizing function when parsing JPEG images had a bug that caused memory allocation issues (integer overflow) during the decompression process.
The generated image file can contain a payload capable of using Instagram’s extensive list of permissions on a mobile device, granting access to "any resource on the phone that is pre-authorized by Instagram," the team says.
This may include access to the device’s phone contacts, location/GPS data, camera, and locally stored files. In the Instagram app itself, the RCE vulnerability can also be used to intercept direct messages and read them; delete or post photos without permission or change account settings.
“At the most basic level, an exploit can be used to crash a user’s Instagram app, preventing them from accessing the app until they uninstall it from their device and reinstall it, causing inconvenience and possible data loss,” Check Point added.
The description of the vulnerability was made six months after the private disclosure in order to give most mobile phone users time to accept security updates and reduce the risk of exploitation of the vulnerability.
"We’ve fixed the issue and haven’t found any evidence of it being exploited by attackers," Facebook said. "We are grateful to Check Point for helping us keep Instagram secure."