US chip maker Intel’s classified and confidential documents allegedly resulting from a hack were uploaded today to a public file-sharing service.
20 GB of classified information comes from an unknown source. This was just the first part of a series of Intel leaks.
According to
, developer and reverse engineer who received documents from an anonymous hacker, most of the information should be protected by intellectual property. The developer was informed that the information was stolen from Intel this year.
“They were given to me by an anonymous source who stole them earlier this year, more details about this will be released soon," says Kottmann.
“Most of the information has NEVER been published before and is classified as confidential under the NDA or Intel Restricted Secret,” added the developer.
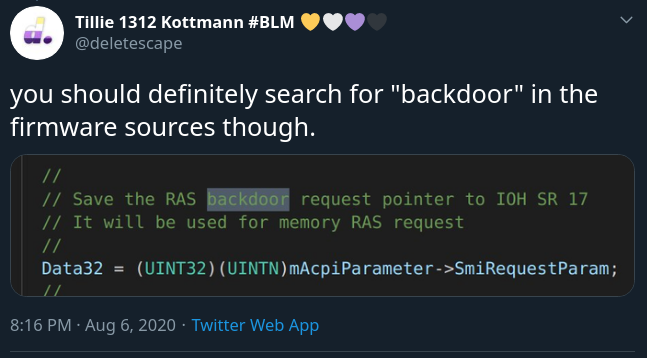
In the source code of the firmware, you can find comments related to backdoors, but this can mean anything and does not necessarily mean that they can access your computer:
An Intel representative pointed to the company’s product security policy page, which states that "Intel’s product development policies and practices prohibit any deliberate steps to allow access to undocumented devices (e.g., ‘backdoors’), disclosure of vulnerable devices." information or circumvention of security features or limitations of its products.”
Some files in the archive contain technical specifications and refer to the internal design of the chipset, including the Kaby Lake platform and the Intel Management Engine (ME).
The first part of the leak contains documents related to the following:
- Intel ME Bringup manuals + tools (flash) + samples for various platforms
- Kabylake BIOS reference code and sample code (Purley platform) + initialization code (some of them as exported git repositories with full history)
- Intel CEFDK (Consumer Electronics Firmware Development Kit (Bootloader)) SOURCES
- Silicon / FSP source packages for various platforms
- Various Intel development and debugging tools
- Simics Simulation for Rocket Lake S and possibly other platforms
- Various road maps and other documents
- Camera driver binaries developed by Intel for SpaceX
- Schematics, documents, tools + firmware for the unreleased Tiger Lake platform
- Kabylake FDK Tutorial Videos
- Intel Trace Hub+ decoder files for various versions of Intel ME
- Elkhart Lake Silicon Reference and Sample Platform Code
- Some Verilog stuff for various Xeon platforms, don’t know what exactly
- Debugging BIOS/TXE builds for various platforms
- Bootguard SDK (encrypted zip)
- Process Simulator Intel Snowridge / Snowfish ADK
- Miscellaneous schemes
- Intel Marketing Material Templates (InDesign)
The release is already being called "juicy," but Kottmann believes that future leaks from their source are likely to contain even more "juicy" classified documents.
How it allegedly happened
Kottman maintains a repository of source code obtained by them and various sources looking for misconfigured DevOps tools that provide access to resources. The repository contains data, including native code, from dozens of companies (GE Appliances, Microsoft, Qualcomm, Motorola, AMD, Lenovo).
The developer goes to great lengths to remove sensitive information from the code they post and comply with takedown requests. Moreover, they are ready to provide detailed information about misconfiguration and how to avoid future failures.
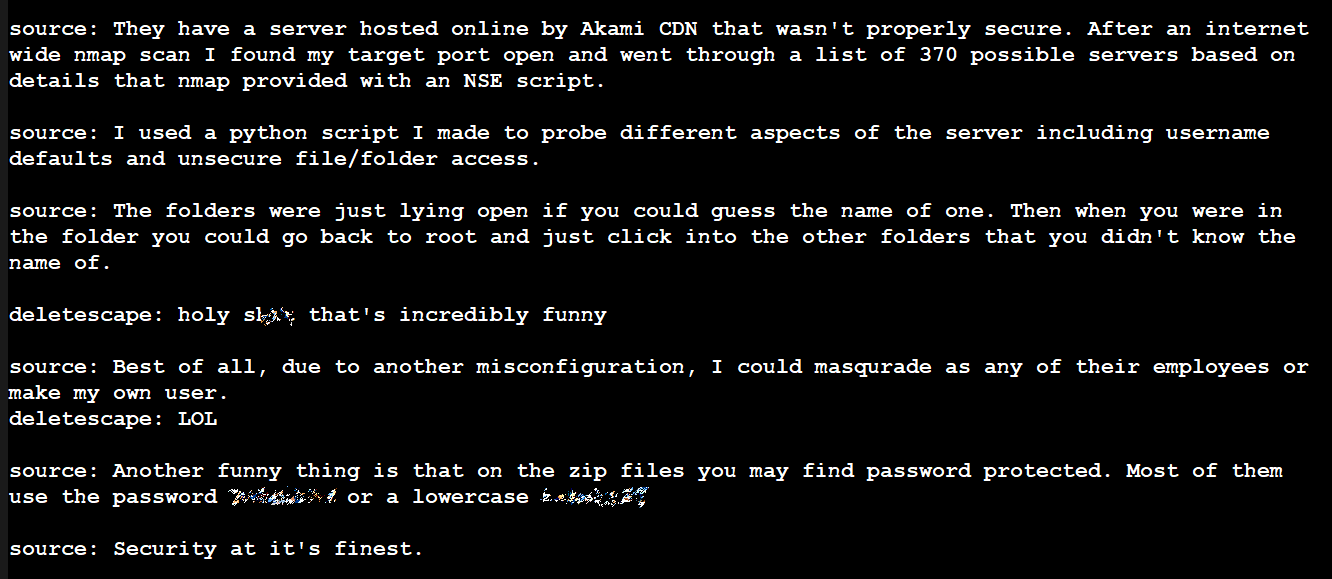
The Intel hack seems to be no different. The hacker told Kottmann that they found an Intel server on the CDN that was not properly secured. This particular machine appears to have been chosen based on parts gathered from web crawls.
Using his own Python script, the hacker claims that he was able to verify username access and unsecured access to files and folders. According to the hacker, access to the folders was possible if you knew the correct names. However, they only had to guess one name. Once inside, they could go back to the root directory and access any of them.
However, the more important detail was the claim that they could impersonate any Intel employee with access to resources or create their own user. Some files are archives protected by incredibly weak passwords.
In a statement to BleepingComputer, Intel said the data appeared to come from the Intel Resource and Design Center. The company spokesman did not elaborate on the method of hacking, but said that the leak could come from someone with access to the portal:
“We are investigating this situation. The information appears to come from the Intel Resource and Design Center, which hosts information for the use of our customers, partners, and other external parties who have registered for access. We believe that the person with access has downloaded and shared this data,” an Intel spokesperson.
Employees in this department have higher privileges than usual, giving them access not only to customer and OEM resources, but also to Intel intellectual property such as documentation and tools, testing services, and product previews, all of which available under corporate non-disclosure. agreement (CNDA).