Why one of the most powerful penetration testing frameworks is dangerous.
Since 2012, Cobalt Strike has been used as a network security testing tool against sophisticated attacker tactics. Unfortunately, like most other security tools and knowledge, Cobalt Strike is also widely used by attackers.
The purpose of this tool is to mimic the most advanced hackers and their methods to test the security of a system. That is why it is widely loved by attackers: from government APT groups to ransomware operators.
In short, this is a powerful network attack platform that combines social engineering , tampering tools, network pattern obfuscation and a sophisticated malware deployment mechanism, and more.
Another leak
Twelve days ago, a repository was created on GitHub that appears to be the source code for Cobalt Strike 4.0, according to BleepingComputer.
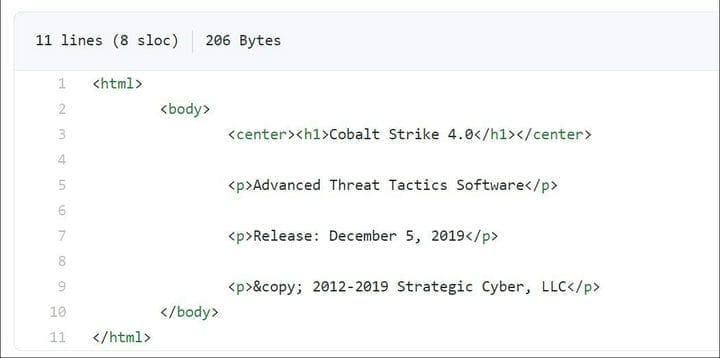
Based on the file src/main/resources/about.html, this version of Cobalt Strike 4.0 was released on December 5, 2019.
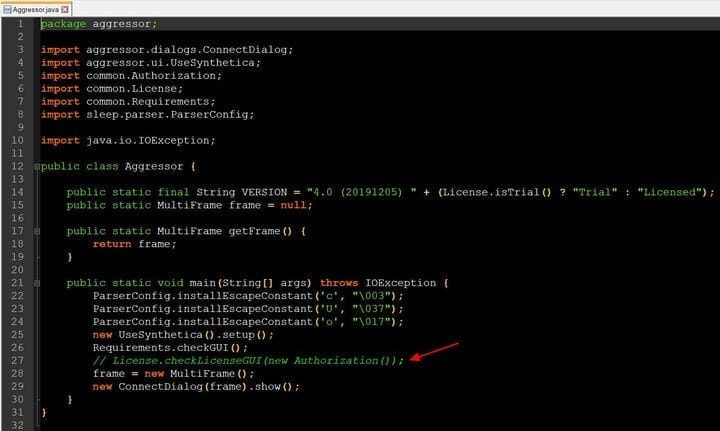
As you can see in the screenshot of the source code below, the license check has been commented out, essentially allowing anyone to compile a full version of it.
Security specialist Vitaly Kremez of Advanced Intel, who reviewed the source code, said he believed the Java code was manually decompiled. The person then fixed all dependencies and removed the license check so it could be compiled.
The repository has been forked 172 times since its publication, making it difficult to curb distribution of source code.
What is Cobalt Strike?
Cobalt Strike is a commercial penetration testing tool that gives security professionals access to a wide variety of attacks.
It primarily allows the delivery and control of payloads to the attacked computer, but in addition, Cobalt Strike can be used for spear phishing, gaining unauthorized access to systems, and can also simulate various malware and other sophisticated attack tactics.
It is a completely legal tool used by ethical hackers and costs $ 3,500 per user. However, it is also widely used by attackers to carry out real attacks on organizations. Some attackers get a trial version of Cobalt Strike and crack its software defenses, while others find leaked cracked versions on hacker forums and shady marketplaces.
Cobalt Strike is a hacker’s Swiss Army knife
Cobalt Strike is a favorite because it is stable and very flexible. It can be repurposed to deploy all sorts of payloads, such as ransomware or keyloggers, on a compromised network. It is well organized and provides a framework for managing compromised assets. Essentially, this tool helps Level B hackers act like Level A hackers .
Cobalt Strike provides the following features:
- Reconnaissance – discovers what software the target is using, with version information to identify known vulnerabilities.
- Attack Packages – provides various social engineering attack mechanisms, creates Trojans, which are innocent files such as Java applets, Microsoft Office documents or Windows programs, and creates clones of websites.
- Collaboration – The framework allows a hacker group to share information and communicate in real time, as well as jointly control compromised systems.
- Post-exploitation – Cobalt Strike uses a payload generation mechanism called Beacon. It allows you to deploy PowerShell scripts, log keystrokes, take screenshots, upload files, and execute other payloads. A beacon can change its network signature to mimic the behavior of various types of malware or impersonate benign traffic.
- Hidden communication – allows attackers to change network indicators on the fly. The tool creates covert channels using DNS, HTTP, HTTPS protocols to prevent network communication detection by standard IDS/IPS systems.
- Flip Browser – can be used to bypass two-factor authentication.
Hacking ATMs with Cobalt Strike
To illustrate the capabilities of this tool, we will give an example of an attack from the Group-IB investigation .
In July 2016, the work of one of the largest banks in Taiwan was paralyzed. The bank faced a massive attack: masked men simultaneously emptied about 30 ATMs in the amount of $ 2 million. The police were at a loss: there were no traces of hacking or overhead devices – skimmers on the cases of ATMs. The attackers did not even use bank cards.
Fortunately, everything that happened was recorded by surveillance cameras: masked people approached ATMs and made phone calls, after which the ATM dispensed money without further ado, which the criminals put in backpacks and ran away. After that, the eight largest banks in the country had to suspend the issuance of cash in 900 ATMs.
What the bank has encountered is called a logic attack. Its essence is that hackers infiltrate the banking network by sending phishing emails with an exploit and, having penetrated into it, establish full control over ATMs. After that, they reproduce the command to issue money. Accomplices of burglars – take the money and transfer it to the organizers of the attack.
The hacker’s tool was precisely Cobalt Strike.
Why is Cobalt Strike a powerful weapon in the hands of hackers?
Even though the leaked source code was not original, it’s enough to seriously worry security professionals, as it removes the barriers to obtaining such a powerful tool and makes it much easier for criminal gangs to acquire and modify code as needed on the fly.
The leak also opens the door for further enhancements to the toolkit by criminals, as happens with many malware tools after a leak, such as Zeus 2.0.8.9 or TinyNuke, as they are now constantly being reused and updated.
BleepingComputer attempted to contact Cobalt Strike and their parent company Help Systems to verify the authenticity of the source code, but received no response.
This is not the first time attackers have managed to hack fully functional versions of Cobalt Strike and make them widely available on marketplaces and dark web forums. For example, back on March 22 of this year, the latest version of the tool was hacked and posted on hacker forums.